 Don’t feel embarrassed about clicking that link – it happens to everyone, even IT pros! Our simulated phishing email was designed, just like the real ones, to get you to click that link.
Don’t feel embarrassed about clicking that link – it happens to everyone, even IT pros! Our simulated phishing email was designed, just like the real ones, to get you to click that link.
Cybercriminals use a variety of tricks to prey on unsuspecting folks and get them to willingly provide information like:
-
- Usernames and passwords
- Banking details
- Credit card numbers
- And more.
Wharton Computing is engaging in this phishing exercise to help you avoid the real thing.
Need help or want more info? Contact the Wharton Information Security Office: security@wharton.upenn.edu
Anatomy of a Phish
There are some basic things that can tip you off to a phishing message:
- Poor spelling and grammar
- Unusually unprofessional messages from organizations or work colleagues
- Strange formatting
The test phishing message you received didn’t have too many of those characteristics, which makes it a pretty believable message. What should you have been on the lookout for?
One of the most effective ways of identifying a phishing email is to verify the email address that the message is from. The message you received purported to be from help.desk (see the image below), which isn’t a real Wharton email address.
There are a few more potential tip-offs in the email. Let’s take a look:
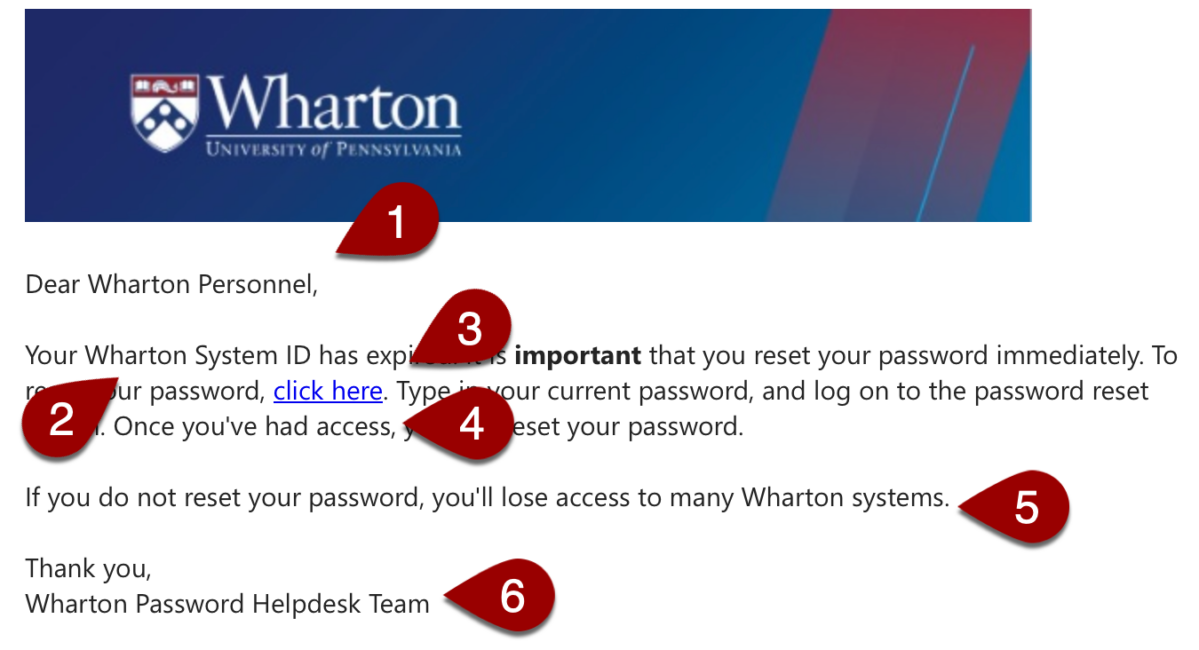
- The salutation of this email is a little off. It is not enough to classify this as a phishing message but an indication that something is happening here.
- “Wharton System ID” isn’t a phrase we use here for any of our accounts. PennKey or Wharton Account would be what one would expect to see in such an email.
- A mysterious link! Hovering over it, or opening it in a browser, shows you that it doesn’t lead to a Penn password-changing website (it leads here, but in an actual phishing message, it would send you to a false password page to harvest your username and password).
- “Had access” isn’t grammatically correct. To be honest, grammar mistakes can occur in legitimate messages, but this is always a red flag.
- Phishing messages often want to instill a sense of urgency to short-circuit your critical thinking skills.
- The “Wharton Password Helpdesk Team” isn’t a real team at Wharton.
When taken on their own, many of these signs might not be enough to be suspicious, but all of them together? Something smells phishy.
If you have any suspicions about an email you receive, you can always contact the Wharton Information Security Office (security@wharton.upenn.edu). Be sure to include the email message you have questions about, and they will happily help.
Additionally, your Wharton Computer representative is available if you have any questions about an email or any other technical issues.
How to avoid being a phishing victim
Sending email is cheap, which is why phishing is an effective activity. Cybercriminals send out millions and millions of these messages, and even if a very small percentage of recipients are fooled the math works out in the criminals’ favor.
Here are few things to be on the lookout for if you suspect an email is actually a phish:
- A sense of urgency – Phishing emails are designed to make you take action before you do anything else. The cybercriminals don’t want you to think too much, or follow lists like this one!
- Mistakes and vagueness – Many phishing emails are littered with misspellings, signatures with incorrect contact information, and the wrong phrases for common internal groups (University IT instead of Wharton Computing, for example).
- Unusual links – If you do click links in an email, pay close attention to where the link is actually sending you. Many phishes will send you to a page that looks like a login screen you’re familiar with (the PennKey login, for example), but if you look at the URL bar of your browser you’ll see you’re not on any of Penn’s websites.
Phishing emails are increasingly a vector for attack, but there are a few things you can do to make yourself a harder target:
- Double check the sender – Criminals can easily make it look as though an email is coming from your boss, so double check that the email is from who it seems to be from. This is doubly true if the email is asking you to do something out of the ordinary like buy gift cards, reset your password, or something similar.
- Check the email for the common signs of phishing – As outlined above, just taking a few moments before acting on an email to consider if it is legitimate will foil most phishing attacks.
- Avoid attachments – Attaching things to email is very easy, which is exactly why the criminals use the technique. Leverage file sharing services like Box and Dropbox instead of attaching things to email.
- Type in URLs – If you think an email looks suspicious, but you want to make sure the account it references is OK, just type in the URL of the service you want to log into instead of clicking on the included link.
What to do if you have been phished
Phishing emails are generally designed to do one of two things: Get your username and/or password or install some malicious software onto your computer.
The first thing you should do if you suspect you’ve been a phishing victim is: don’t panic. Stay calm. Wharton Computing is here to help you.
Secondly, inform your Wharton Computing representative as soon as possible. They will help you with the following:
- changing your password(s)
- determine if malicious software has been installed
In either case, time is of the essence; the longer you wait, the harder it will be to recover.
What is Phishing?
Phishing emails are scams designed to trick you into giving cybercriminals access to your accounts or valuable information about you. They often appear to be from a legitimate source like an administrator of your email system or someone you know.
The contents of phishing messages are generally designed to create a sense of urgency by asking you to perform an action of some kind, like:
- warning that your account may close if you don’t use your account credentials to log into their website
- call to click on a link to address financial or other issues
- request to update your work data
Phishing attempts are getting increasingly sophisticated and while we block many phishing attempts, no system is 100% effective. Please follow the recommendations on this page to identify, and thwart, any phishing attacks that end up in your email box.


